In the IT World we have had, over time, many examples of correct models but incorrect implementations.
An example? You think about implementing Wep key-based authentication in Wifi solutions. The reference mathematical model is correct but the implementation of the RC4 cipher is incorrect (see IV attack).
Another real case
For Cybersecurity reasons, I used Burp Suite to analyze a strange (and in my opinion incorrect) implementation of 2FA authentication used to log into a production web-site that manage sensitive data .
To access (logon) the site you need to enter your username and the otp password received via text message (sms).
ANALYSIS
The site in question supports TLS protocol (https) but this is not a problem. Just use the right tools.
On my system used as a client, I have activated the proxy mode and the intercept function.
The basic technique used is MITM (Man in the Middle Attack) to analyze the traffic between client and server.
According to the developers of the service, a “halfway” 2FA implementation is (in) correct: I enter my username (which may be known by other people) and the service sends me a text message (sms) with an otp password to access the site.
From the point of view of cybersecurity, the problem is not being able to read the sms message (we don’t care) but “guessing” the otp.
It is easy to notice that the otp password in question is composed of only numbers and (only) 5 elements.
The implementation choice of using an otp password of only 5 numeric characters does not comply with the provisions of the legislator and the GDPR which, on the other hand, indicates that for sensitive data it is necessary to use at least an alphanumeric password of 8 characters. This choice is the first step to lower the security level of the analyzed site.
It seems that the developers of the service have (sadly) decided not to set a password entry limit nor an otp password expiration time.
We can, therefore, use a quick bruteforce (otp of only 5 numeric characters) to find the password.
ATTACKS
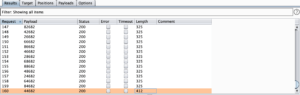
We use the Burp Suite Intruder feature to perform our bruteforce.
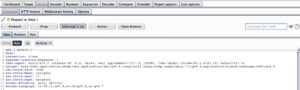
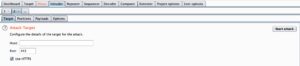
Configure the target.
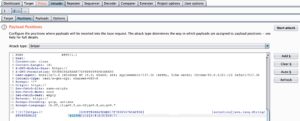
Select Sniper Attack and set the password as a variable (see photo and you must use special character).
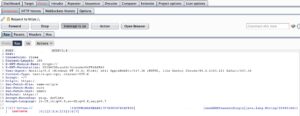
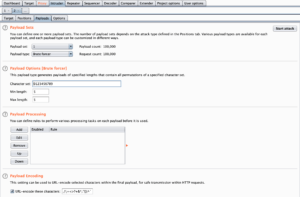
In Payloads Tab select:
- Brute Force Attack.
- Only 0123456789 characters.
- Password min lenght: 5 character
- Password max lenght: 5 character
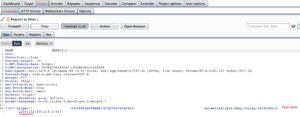
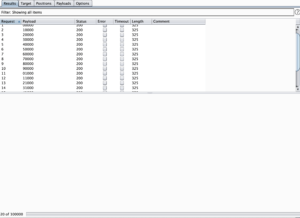
Start Attack (max 100000 tries).
The correct password (44682) has response length page different (412 byte).
CONCLUSIONS
The secure code needs (cyber) security by design, nothing else matters.
If the saying “Attacks always get better” is true then we should have greater awareness and improve sensitive data management techniques.